This post covers the IBM Redbook: Using the IBM Security Framework and IBM Security Blueprint to Realize Business-Driven Security published in April 2013.
This book provides an introduction to the IBM security framework and blueprint. I do not cover this here because I previously covered it in my post Managing Security and Compliance in Cloud or Virtualized Data Centers.
Business Context
From the red book: “Business and IT drivers influence security. Business drivers measure value, risk, and economic costs that influence an organization’s approach to IT security. Value drivers determine the worth of assets of the system to the business and of the business itself. Risk drivers involve compliance, corporate structure, corporate image, and the risk tolerance of the company. Economic drivers determine productivity impact, competitive advantage, and system cost.
IT drivers represent operational constraints in the general IT environment. For example, the complexity of a system, including its environment, that is exposed to internal and external threats presents risks that the organization must address. The IT drivers represent technical considerations that can affect the trustworthiness of the IT environment and the managed business systems as a whole. IT drivers are universal and must be considered within the context of the business drivers in all efforts. The combination of business and IT drivers represents the key initiatives for security management.”
The following business drivers are covered:
- Correct and reliable operation
- Service level agreements
- IT asset value
- Protection of the business asset value or brand image
- Legal or regulatory compliance
- Contractual obligation
- Financial loss and liability
- Critical infrastructure
- Safety and survival.
The following IT drivers are covered:
- Internal threats
- External threats
- IT service management commitments
- IT environment complexity
- Business environment complexity
- Audit and traceability
- IT vulnerabilities.
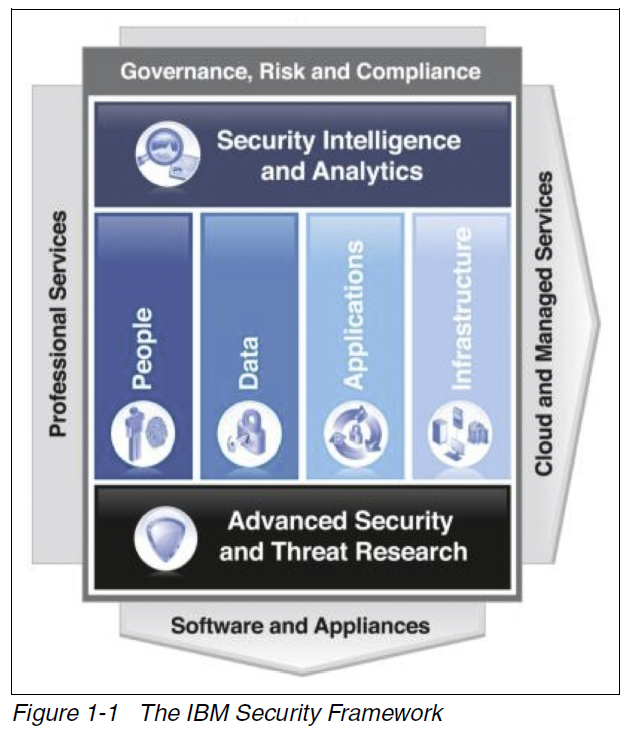
IBM Security Framework
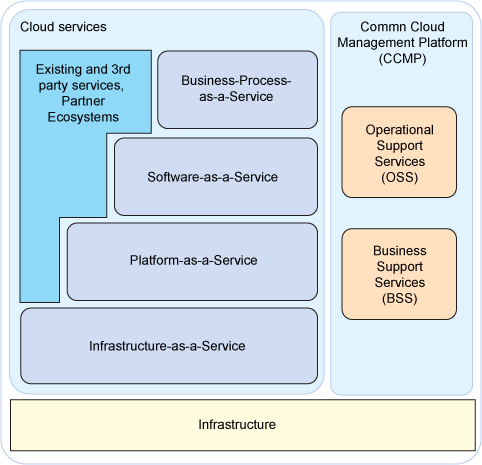
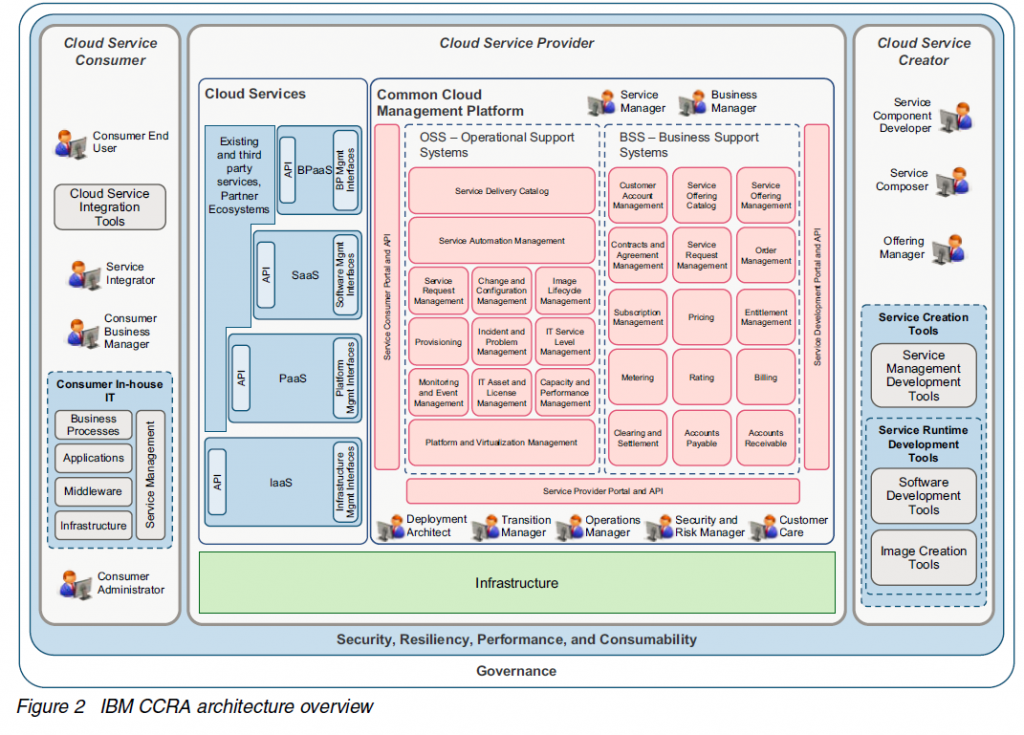
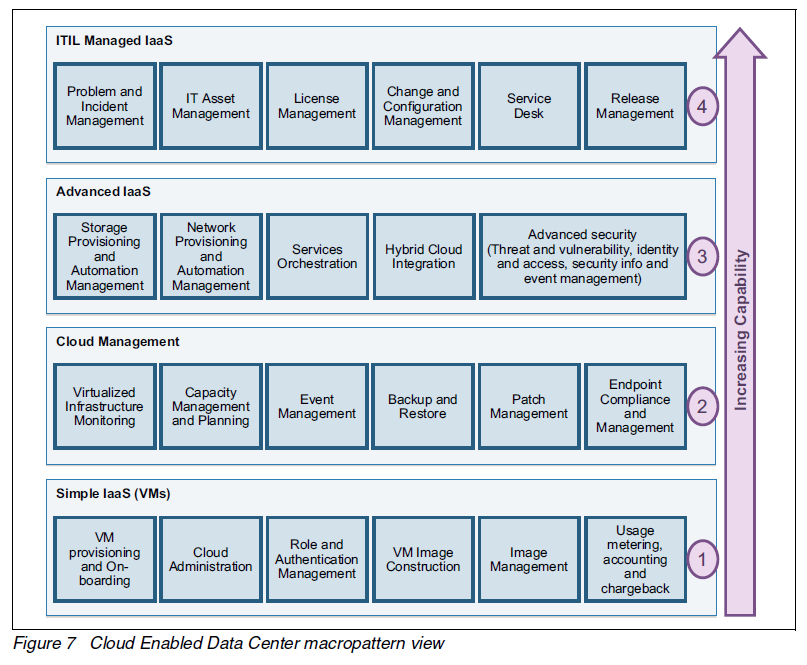
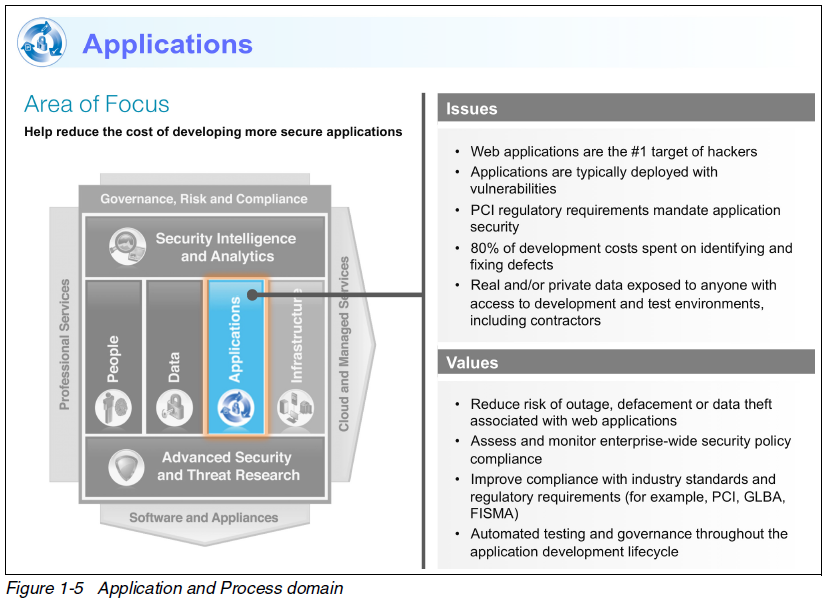
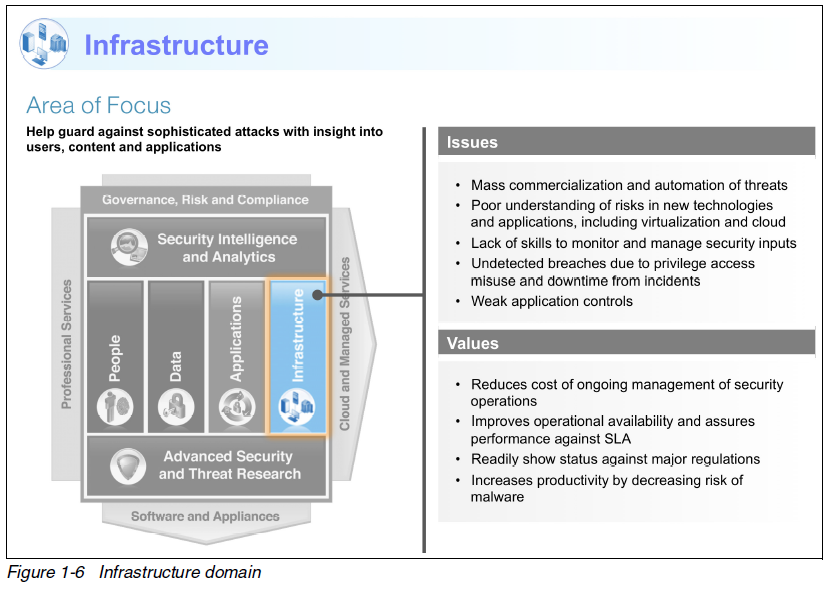
The IBM security framework covers the breadth of security. I show applications and infrastructure here.
For infrastructure, and important point is the decision to use virtualization. “Organizations are increasingly using virtualization technology to support their goals of delivering services in less time, with greater agility, and at lower cost. By building a structure of security controls within this environment, organizations can reap the goals of virtualization, such as improved physical resource utilization, improved hardware efficiency, and reduction of power costs, while they ensure that the virtual systems are secured with the same rigor as the physical systems.”
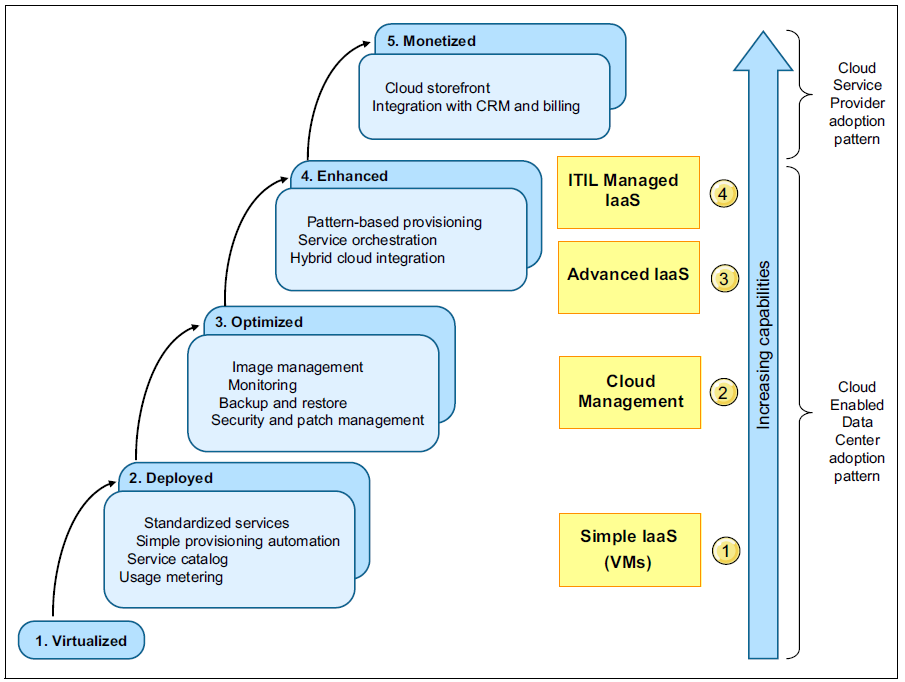
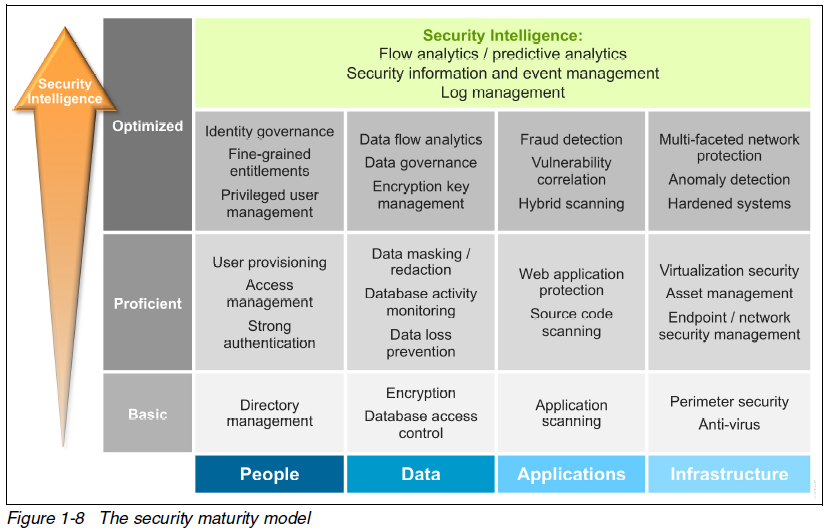
Security Maturity Model
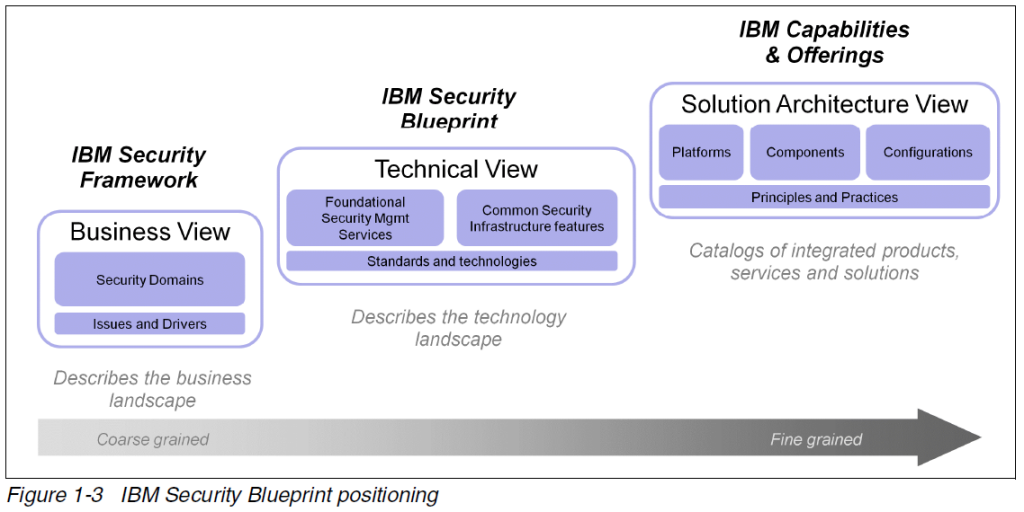
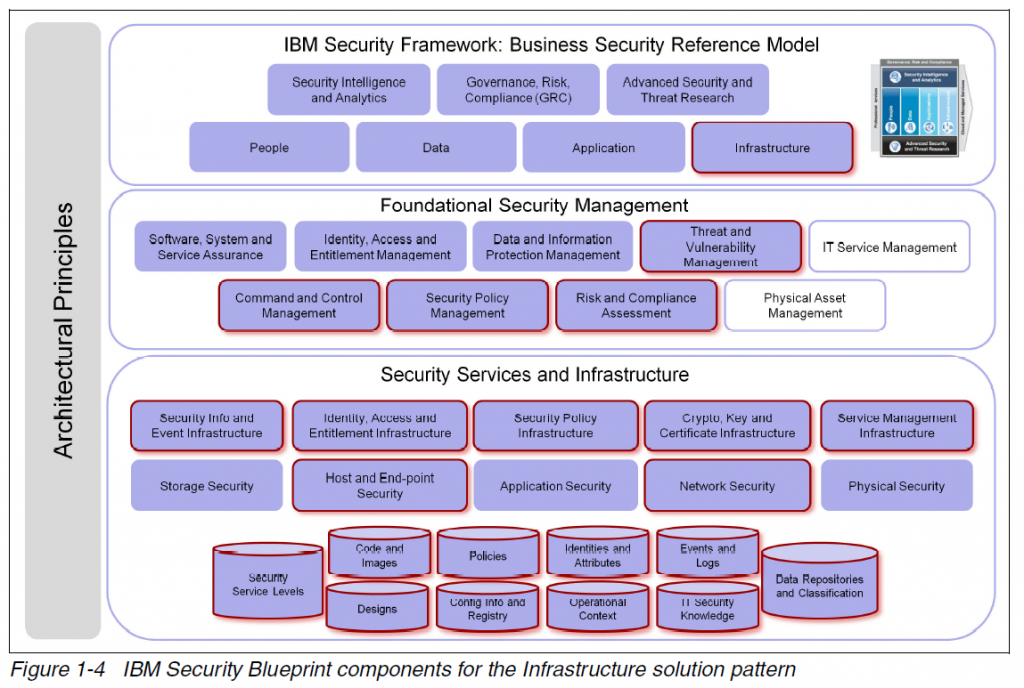
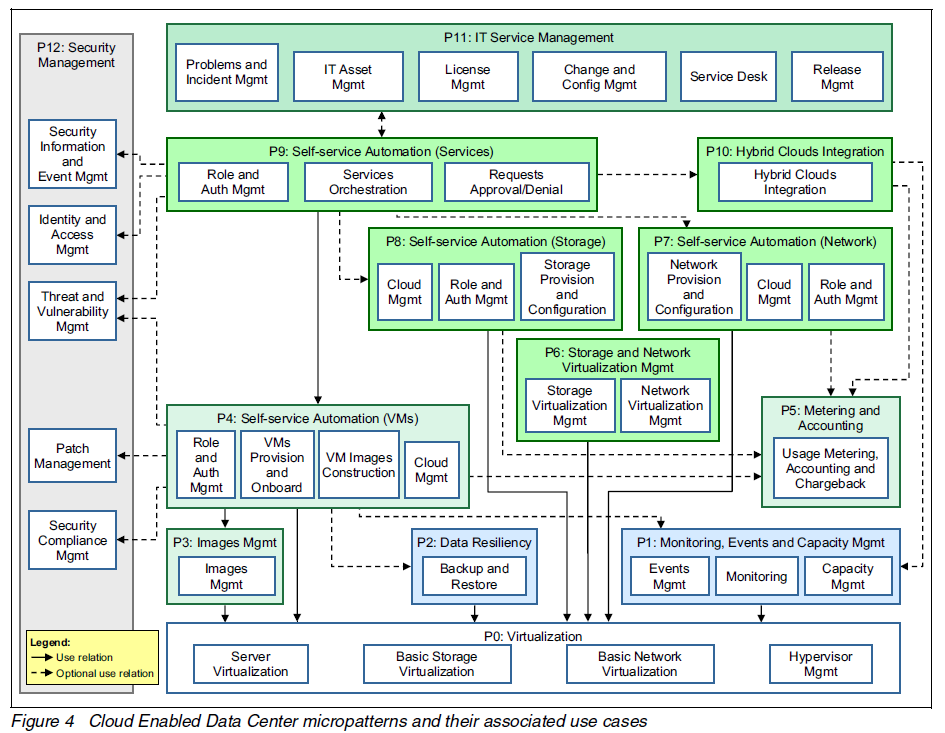
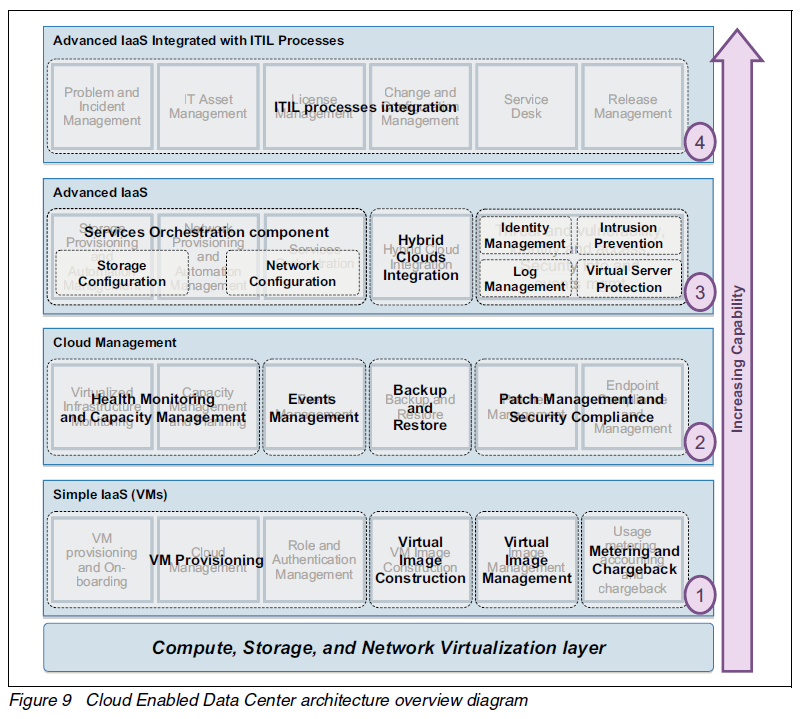
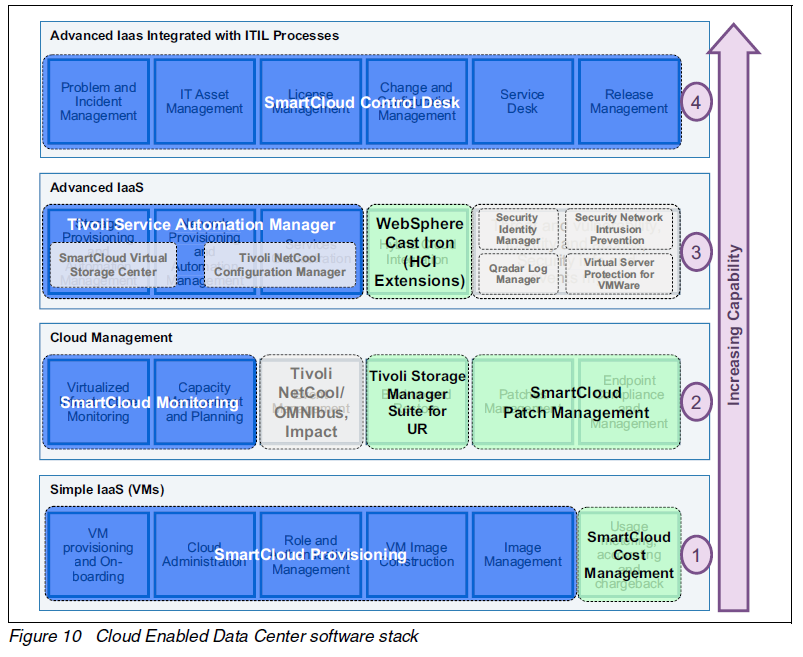
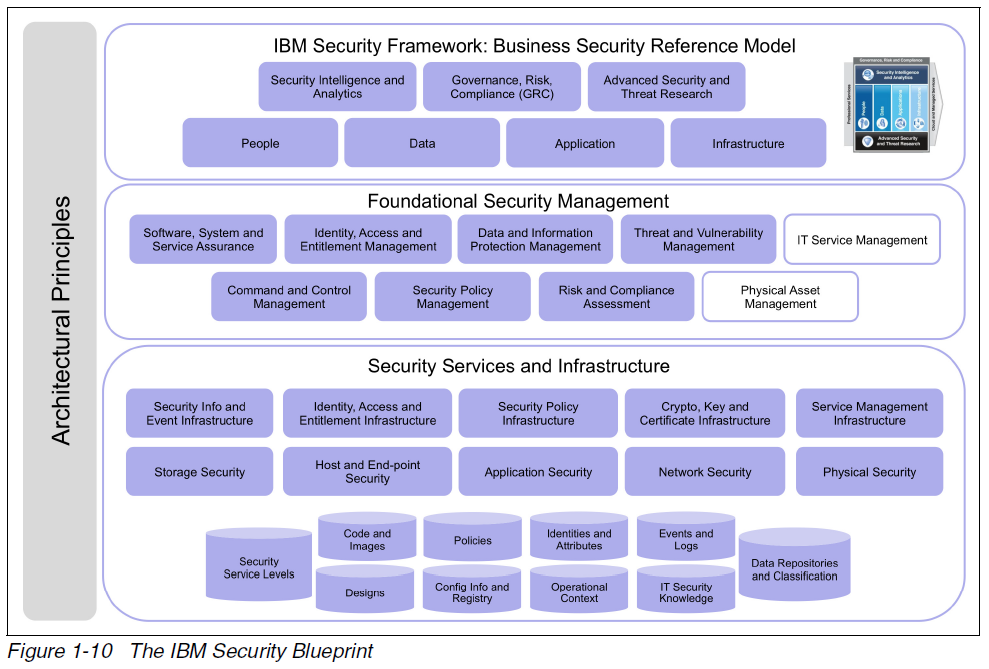
Security Blueprint
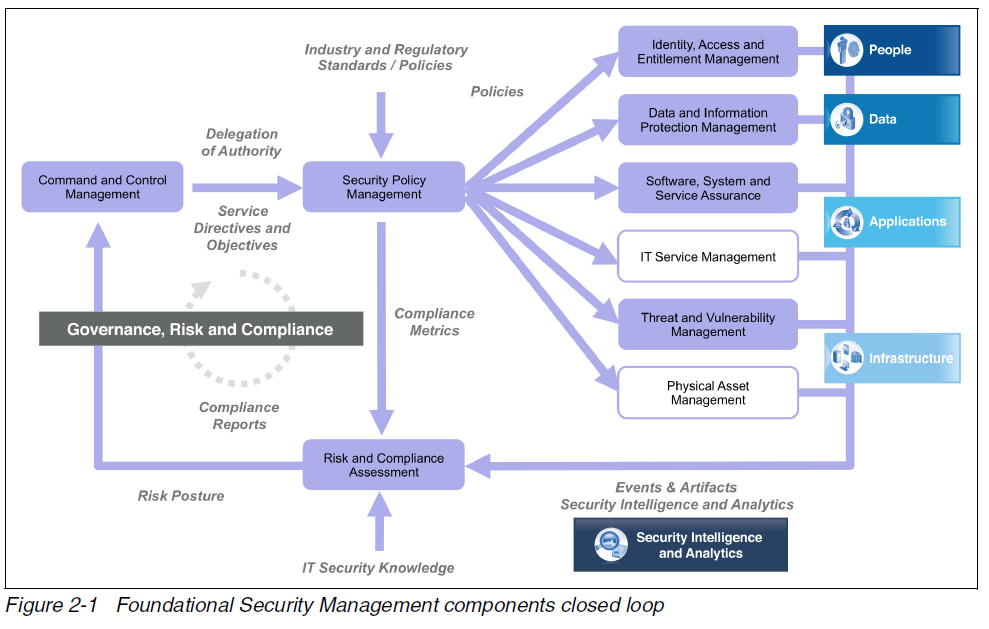
�The Security Blueprint has the following foundational components:
- Command and Control Management
- Security Policy Management
- Risk and Compliance Assessment
- Identity, Access, and Entitlement Management
- Data and Information Protection Management
- Software, System, and Service Assurance
- Threat and Vulnerability Management
- IT Service Management
- Physical Asset Management.
Architecture Principles
The following architecture principles are covered:
- Openness�
- Security by default
- Design for accountability�
- Design for regulations�
- Design for privacy�
- Design for extensibility�
- Design for sharing
- Design for consumability�
- Multiple levels of protection�
- Separation of security management, enforcement, and accountability�
- Security-critical resources and awareness of their security context�
- Model-drive security�
- Consistency in approaches, mechanisms, and software components.
Foundational Security Management
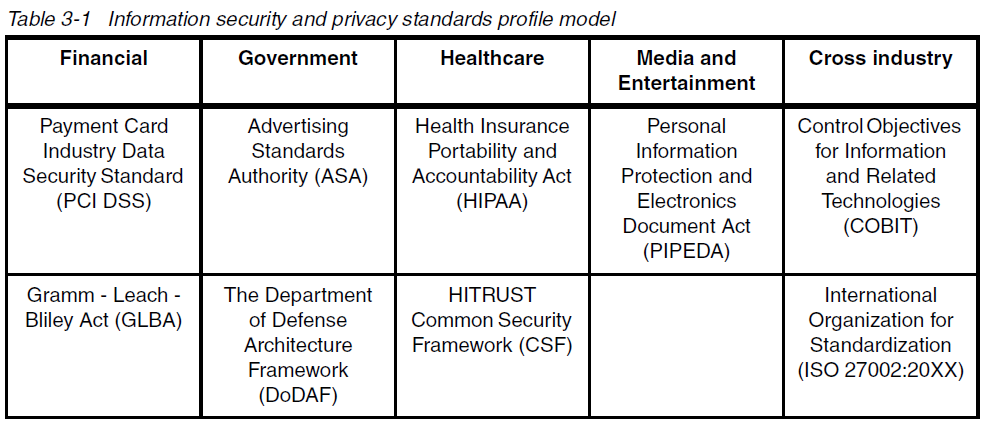
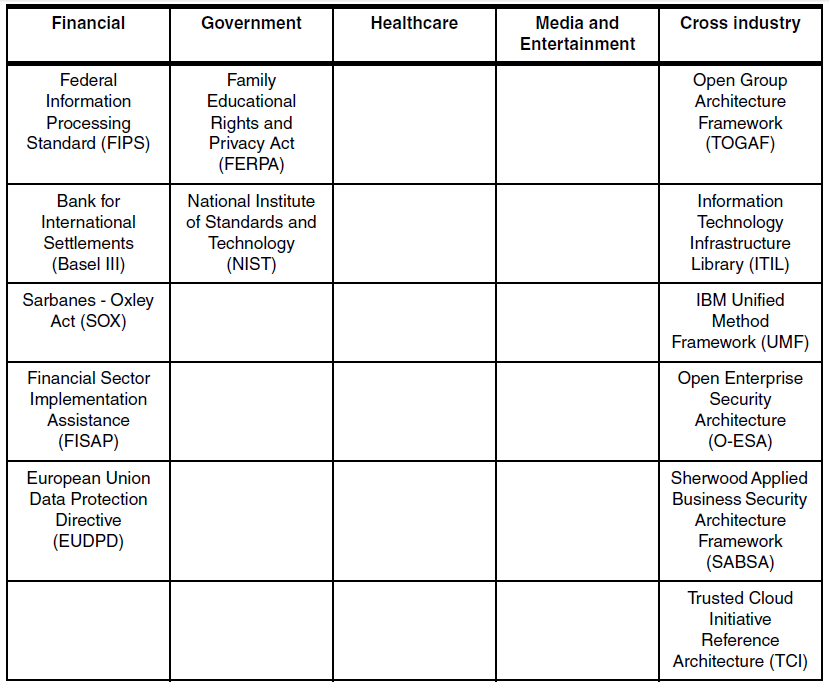
Security Frameworks and Standards
Frameworks include:
Standards in the Industry information security and privacy standards profile model:
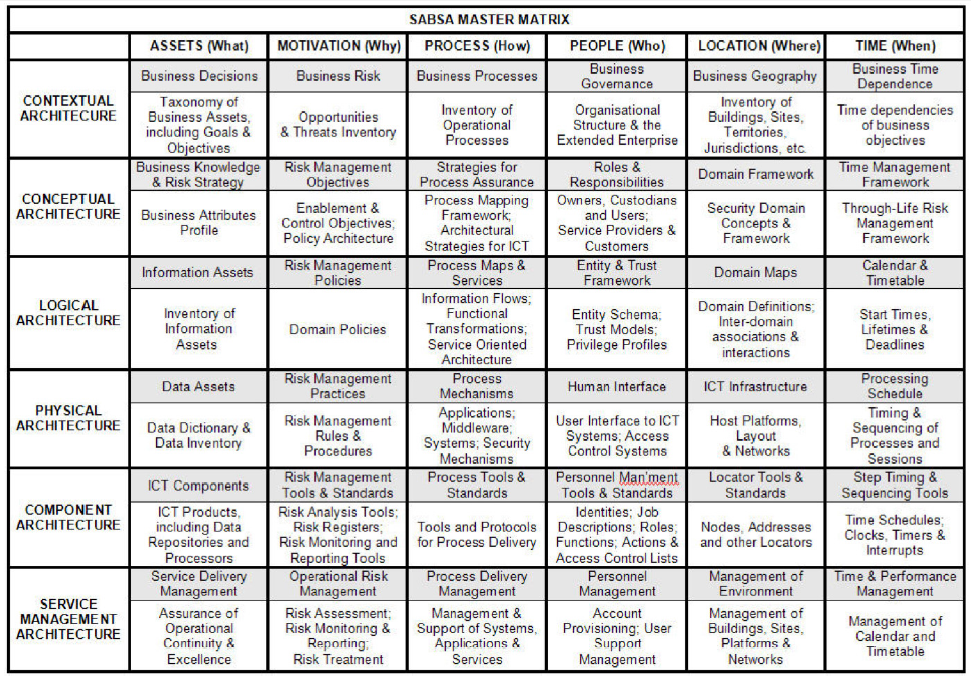
SABSA
SABSA looks at the following business requirements:
- Low-cost development�
- Fast time to market
- Scalability of cost�
- Scalability of platforms
- Scalability of security level
- Scalability of use
- Reusability
- Operations costs
- Administration costs
- Usability
- Interoperability
- Integration
- Supportability
- Risk-based cost and benefit effectiveness
- Enabling business.
ISO/IEC 27002:20xx
ISO/IEC 27002:2005 contains 12 categories, or domains, that must be
considered when you apply an overall enterprise security approach. The
categories are:
- � Risk assessment
- � Security policy
- � Organization of information security
- � Asset management
- � Human resources security
- � Physical and environmental security
- � Communications and operations management
- � Access control
- � Information systems acquisition, development, and maintenance
- � Information security incident management
- � Business continuity management
- � Compliance.
O-ESA
The red book describes how to use the Open Enterprise Security Architecture (O-ESA) from the Open Group to build an over-arching Enterprise Security Architecture (ESA).
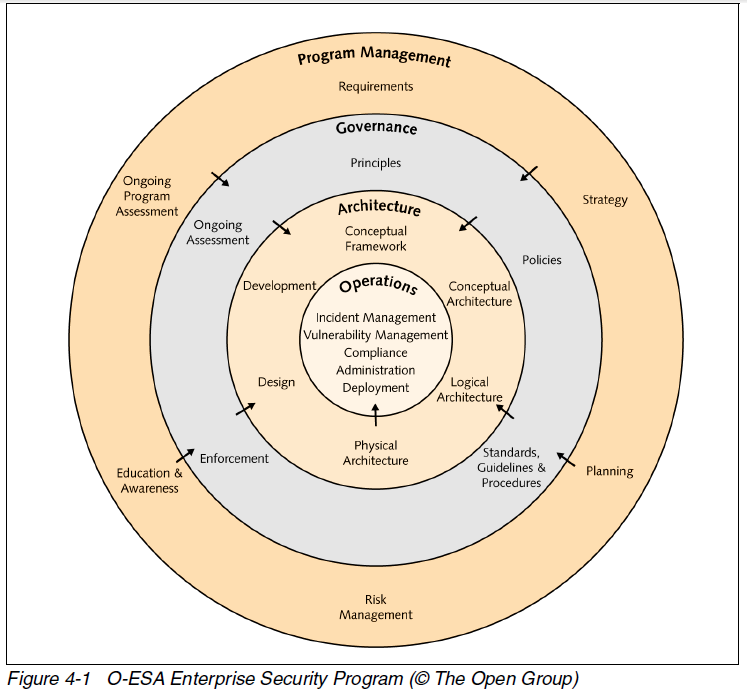
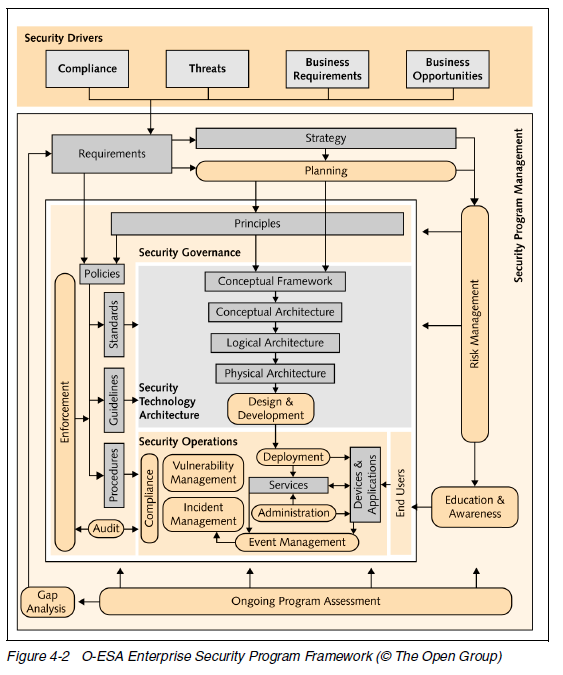
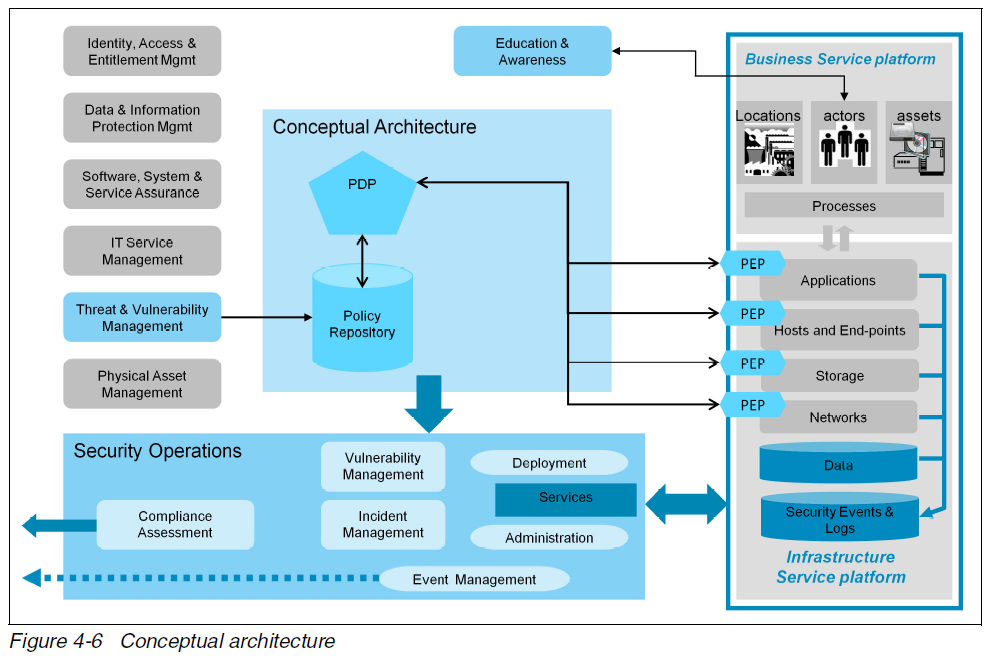
Policy Enforcement Points (PEPs) are included in the conceptual architecture:
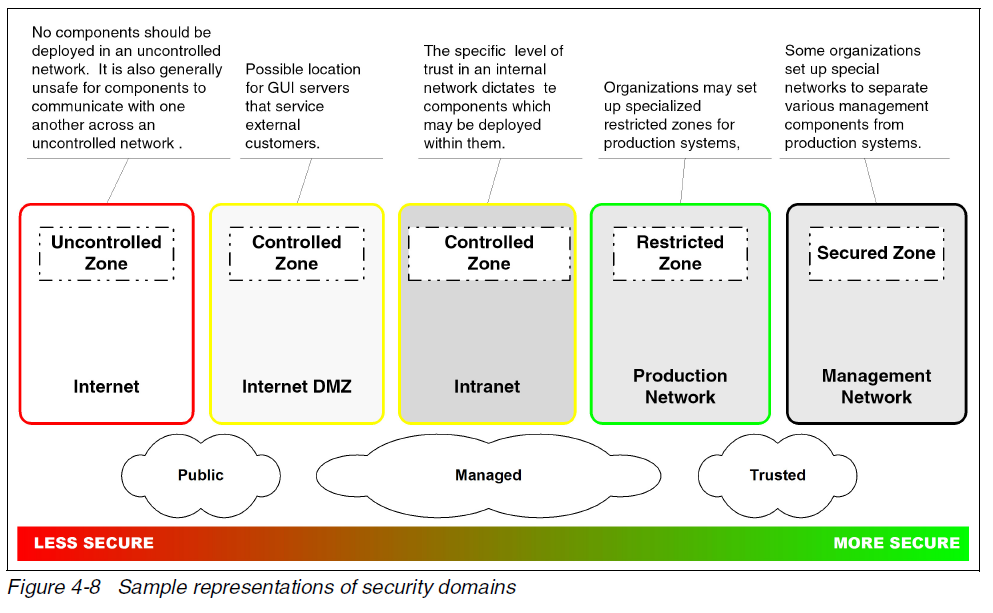
Example security domains are suggested:
- � Uncontrolled
- � Controlled (DMZ)
- � Restricted
- � Secured
- � External Controlled (3rd party).
A process is provided to develop the technology architecture:
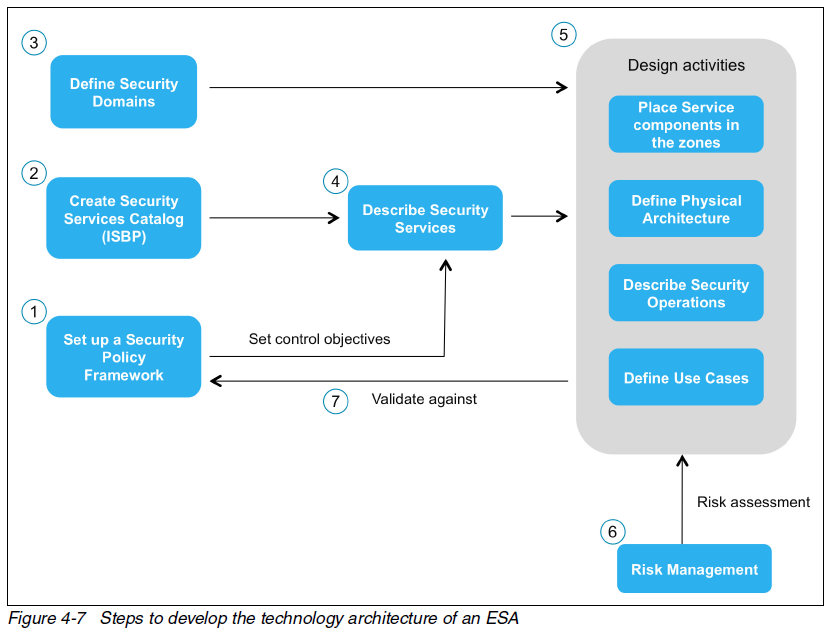
Setting up security zones is summarized and the reader is referred to another red book for details: Enterprise Security Architecture Using IBM Tivoli Security Solutions, SG24-6014. However, this document was written back in 2007. I would take a look at Addressing Emerging Threats and Targeted Attacks
with IBM Security Network Protection (redp4826) first.
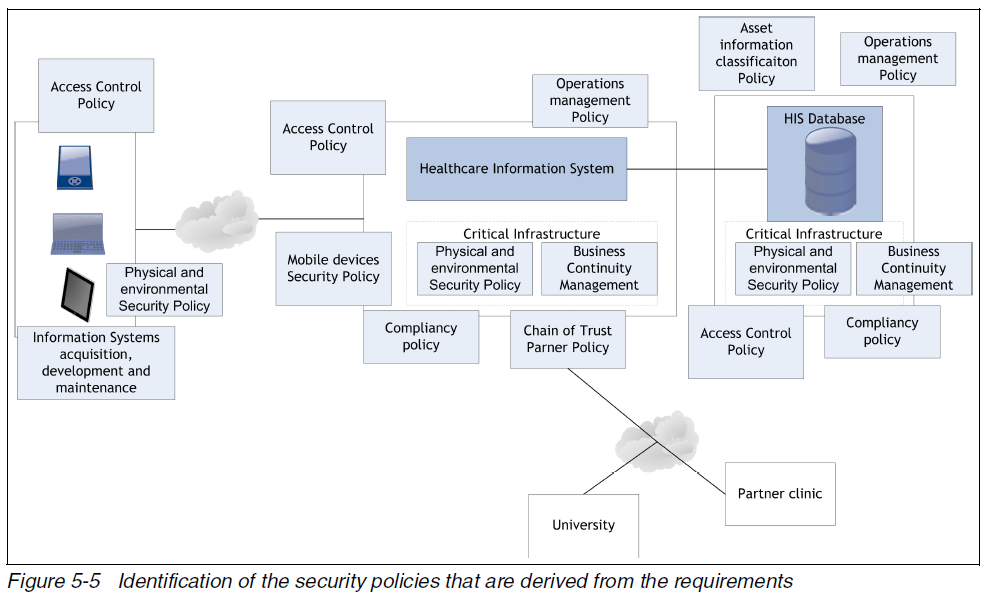
An example is provided for healthcare mobile security where an example set of security policies are provided:
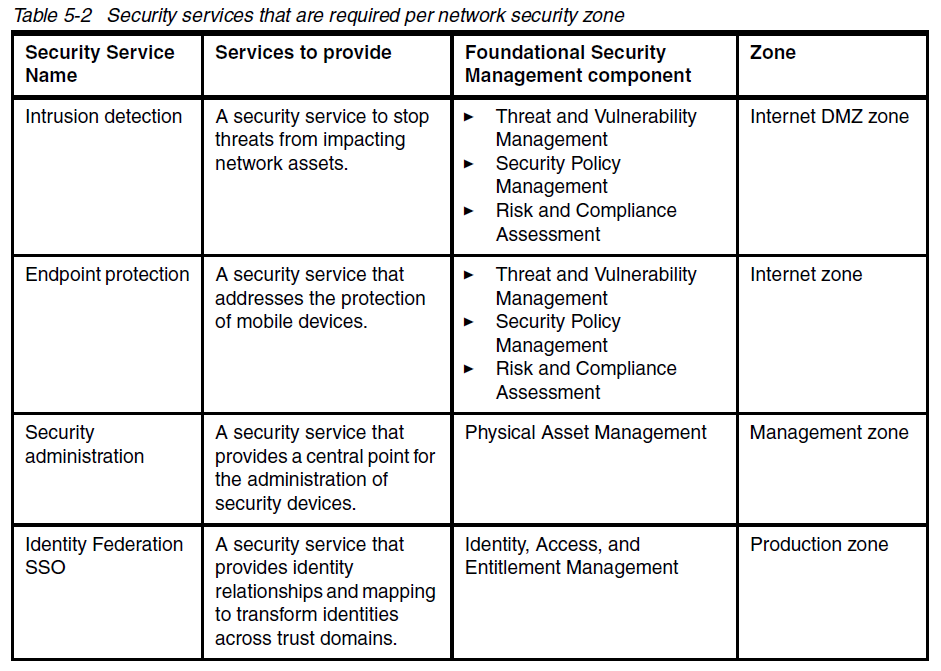
Example allocation of security services to zones is provided:
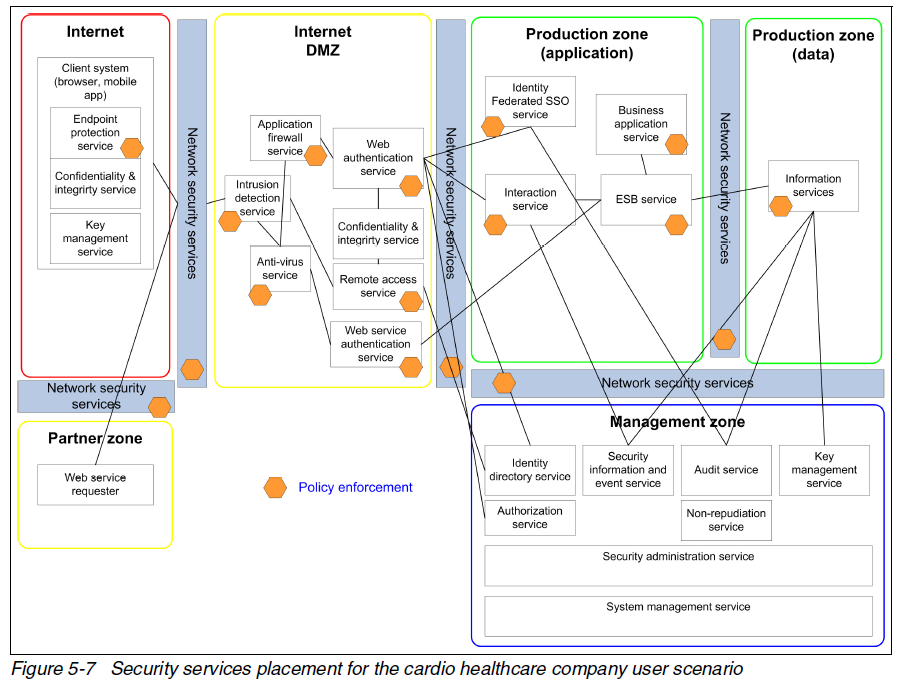
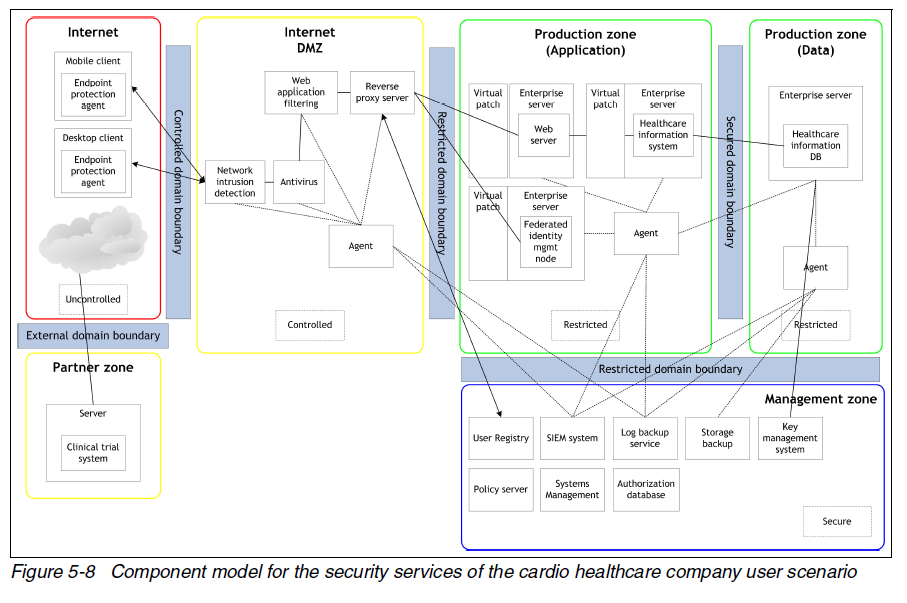
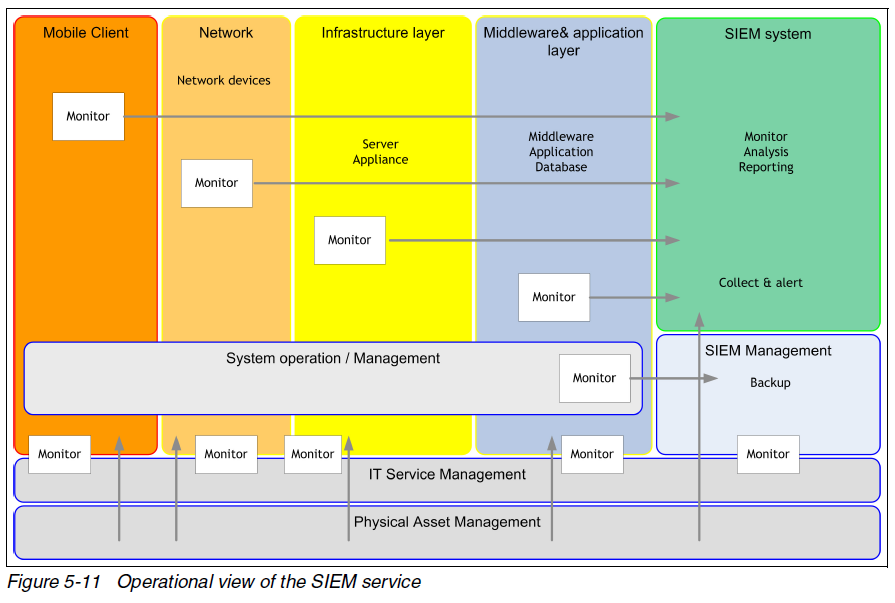
The red book introduces SIEM technology:
“Centralized log collection, analysis, and reporting on compliance for the Health Insurance Portability and Accountability Act (HIPAA), the Payment Card Industry Data Security Standard (PCI DSS), Sarbanes-Oxley Act (SOX), and ISO/IEC 27002:2005 is enforced by using Security Information and Event Management (SIEM) technology. This technology integrates the Web Security Server infrastructure. It also offers operating system-level monitoring that can collect logs from critical UNIX, Linux, and Windows servers. The SIEM solution is also able to monitor the network traffic flows between the components for abnormalities (unusual behavior) and identify data structures that are moving across the wire.”
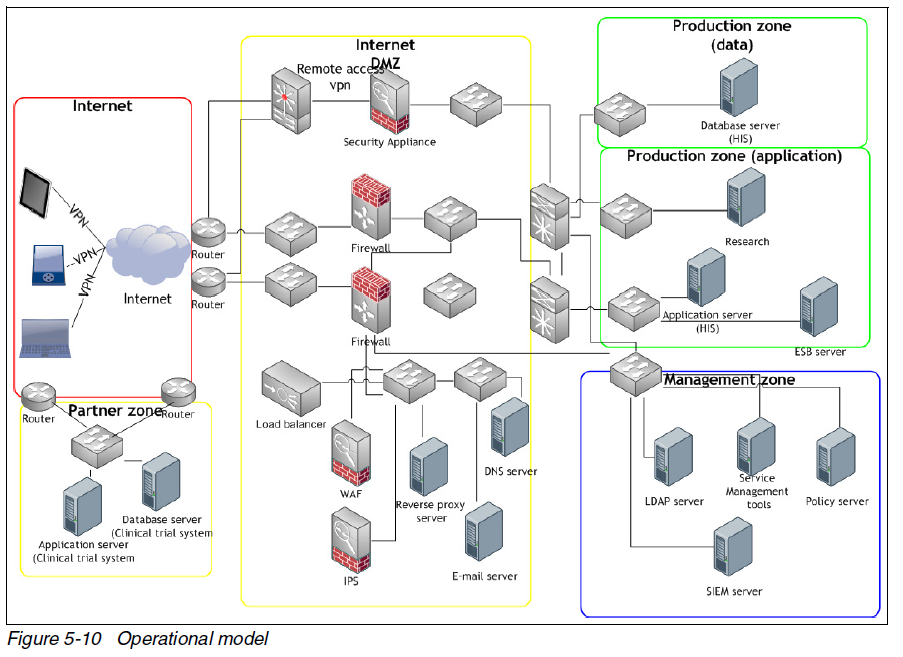
An operation model is provided for the example:
An SIEM operational view is provided: