In this post I cover the IBM Red Book SG248082: Managing Security and Compliance in Cloud or Virtualized Data Centers.
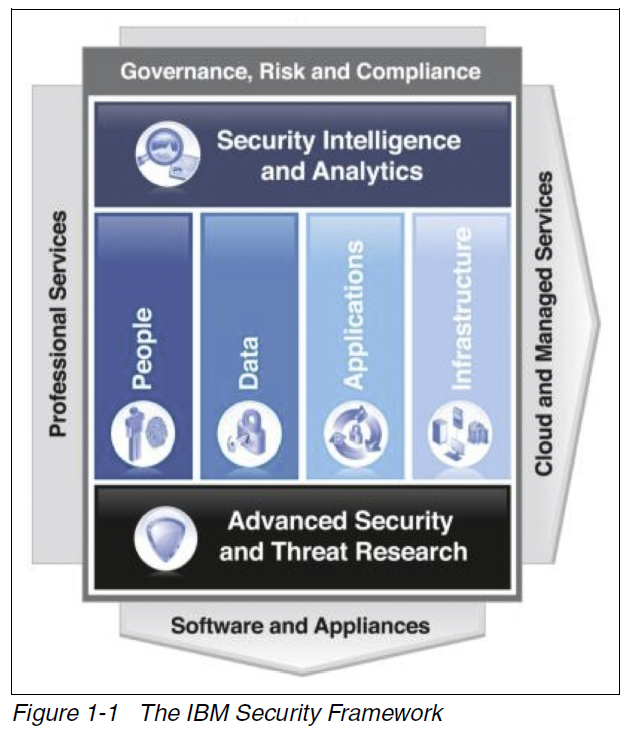
The IBM Security Framework provides a top-level view on security:
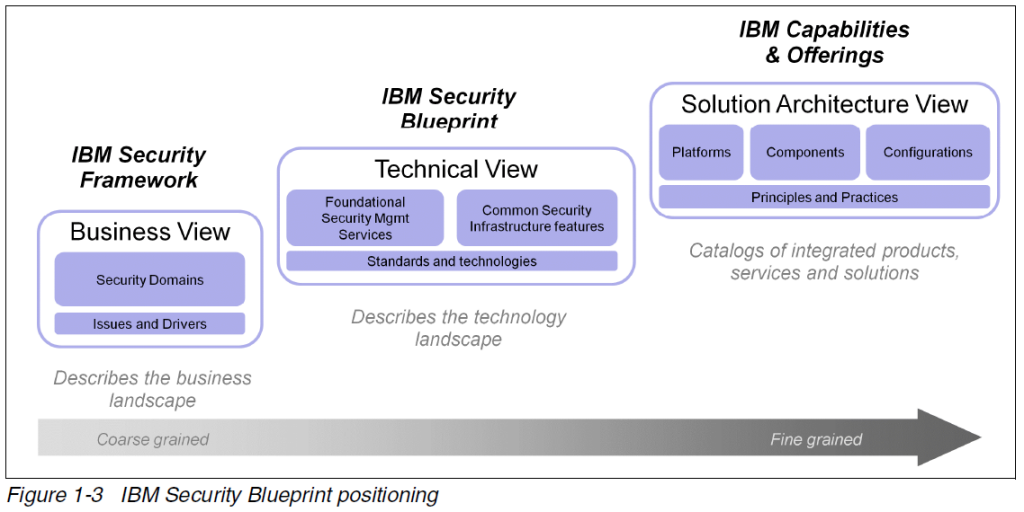
At the second level of detail IBM provides Security Blueprint.
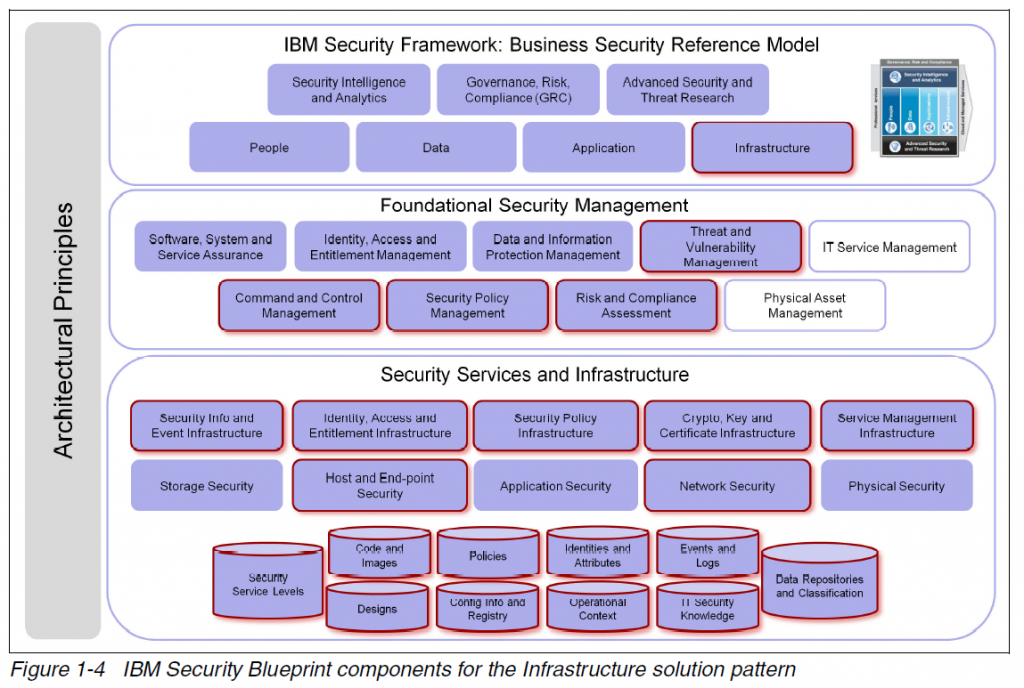
The Security Blueprint categorizes and defines security capabilities and services that are required to answer the business concerns in the IBM Security Framework such as infrastructure.
The Security Blueprint emphasizes control (knowing where you are in and out of compliance, why, and having action plans) in addition to compliance. There is also a focus on visibility into and managing the security of virtual machines.
I cover the IBM Security Blueprint in more detail in my post Using the IBM Security Framework and IBM Security Blueprint to Realize Business-Driven Security.
The functions of the PowerSC products are described and these provide a good example. Regulatory compliance to industry standards such as Payment Card Industry Data Security Standard v1.2 (PCI-DSS) and Control Objectives for Information and related Technology (COBIT), typically adopted subject to the US Sarbanes-Oxley Act, can be automated. Automated compliance helps address the huge effort of staying in compliance with multiple regulations. Trusted Boot is a virtual implementation of the Trusted Platform Module (TPM) from the Trusted Computing Group. Trusted Firewall filters traffic between VLANs. Trusted Logs prevents modification of log files. Trusted Surveyor provides consolidated security reporting.
Pingback: A Top-Down Summary of Cloud Computing Reference Architectures | Alan Street
Pingback: Reading List: Using the IBM Security Framework and IBM Security Blueprint to Realize Business-Driven Security | Alan Street
Pingback: Alan’s Reading List Summary | Alan Street