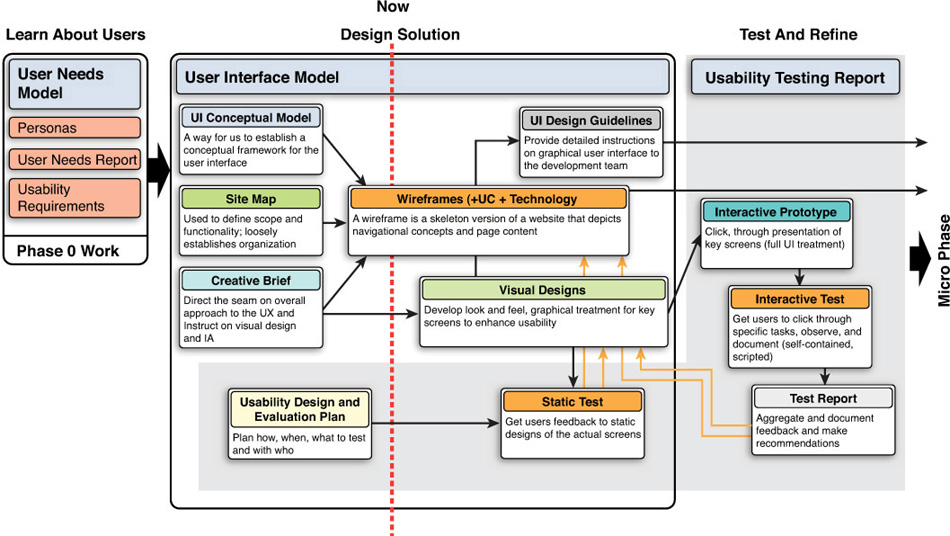
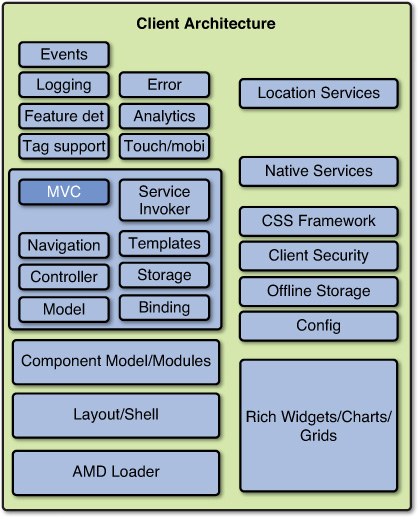
The PCI Security Standards Council provides the PCI Data Security Standard (PCI DSS). Certain organizations including financial services providers need to be compliant with this standard as evidence that they protect payment card holder data (CHD).
The first step to applying the standard is to determine the portion of the IT environment where the standard is applicable (scope). The PCI/DSS scope is called the Cardholder Data Environment (CDE) and includes “people, processes and technologies that store, process, or transmit cardholder data or sensitive authentication data.” Network segmentation is the recommended means to reduce the scope as much as possible.
pcisecuritystandards.org breaks the standard down into 6 categories and 12 requirements:
- Build and Maintain a Secure Network and Systems
- Requirement 1. Install and maintain a firewall configuration to protect cardholder data
- Segment the network to reduce exposure and scope of PCI assessments using firewalls and routers. Separate the internet, DMZ, wireless networks, and internal networks from zones containing CHD.
- Install personal firewalls on PCs and mobile devices.
- Control the network and user devices to verify configurations are within policy.
- Requirement 2. Do not use vendor-supplied defaults for system passwords and other security parameters
- Requirement 1. Install and maintain a firewall configuration to protect cardholder data
- Protect Cardholder Data
- Requirement 3. Protect stored cardholder data
- Requirement 4. Encrypt transmission of cardholder data across open, public networks
- Maintain a Vulnerability Management Program
- Requirement 5. Protect all systems against malware and regularly update anti-virus software or programs
- Requirement 6. Develop and maintain secure systems and applications
- Implement Strong Access Control Measures
- Requirement 7. Restrict access to cardholder data by business need to know
- Requirement 8. Identify and authenticate access to system components
- Requirement 9. Restrict physical access to cardholder data
- Regularly Monitor and Test Networks
- Requirement 10. Track and monitor all access to network resources and cardholder data
- Requirement 11. Regularly test security systems and processes
- Maintain an Information Security Policy
- Requirement 12. Maintain a policy that addresses information security for all personnel.